
Sophos UTM mail security has many features, it also supports DKIM (DomainKeys Identified Mail), which allows the UTM to cryptographically sign outgoing messages.
Unfortunately it’s not “that” easy to set up, like any other UTM feature, but that’s not the UTM’s fault
I will try to explain how to make things work here:
Firstly you have to generate som key pairs, which we need to use to identify your mail, I will be using OpenSSL here, but many other programs are available for Linux and Windows, ex. ssh-keygen or Puttygen.
So go ahead and download this: https://indy.fulgan.com/SSL/
Time of writing openssl-1.0.2l-x64_86-win64.zip is the newest build.
Unzip this to your harddrive and put all the files in c:\openssl-win64
Now create a batchfile called dkimkey.bat and paste the following into it:
@echo off IF EXIST rsa.private.%1 GOTO exists C:\openssl-win64\openssl genrsa -out rsa.private.%1 1024 C:\openssl-win64\openssl rsa -in rsa.private.%1 -out rsa.public.%1 -pubout -outform PEM echo Files created for %1 GOTO done :exists ECHO Files for %1 not created because they already exist. ECHO Please, erase them or try a different name. ECHO . :done
(1024 bits encryption is used here, you must NOT choose a lower value, 2048 is also possible, but some MTA’s may have problems with higher bit value a the moment)
Open a command prompt and change to the folder, where you put the batch file ex. c:\openssl-win64:
and run it: “dkimkey.bat yourdomain.com” ex. dkimkey.bat martinsblog.dk

You can safely ignore the warnings.
After this, you will see two new files in the folder:

Save thoose two files for backup, if you will need them in the future (and youwill )
Open the rsa.public filew in a text editor, and remove all headers and carriage returns from it:
Before:

After:

And NO, theese are not my original files, just demo files for this article
Configure til UTM:
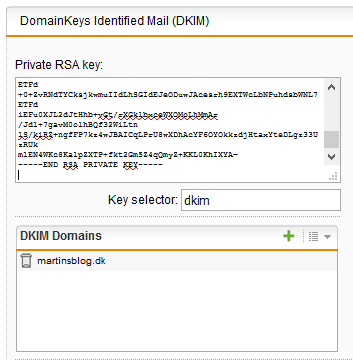
In the Sophos UTM, go to “Mail Security” > SMTP and select the “Advanced” tab and scroll down to DomainKeys Identified Mail.
1) Into the “Private RSA” box, copy the entire content of the rsa.private file.
2) The key selector can be anything you want, here I have choosen “dkim”
3) In the DKIM Domain you need to fill in the domains youwish to apply DKIM for (Remember to have your mailserver relay outgoing mails through the UTM, else this will not work!).
4) Click Apply!
If all is done right, it should look like this:
Now go to your DNS provider for your zone and add the following two TXT records (here martinsblog.dk is used):
TXT record name: _domainkey.martinsblog.dk
VALUE: o=- (Use ~for soft fail DKIM otherwise use “-” for fail, if DKIM is not 100% accurate (recommended)
TXT record name: dkim._domainkey.martinsblog.dk
VALUE: v=DKIM1; k=rsa; t=y; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCnSU957Ycw/2n/kkHEgVWzQ4fK
0eUs5dbNFnPxFhzlVahy/k4KMcTiPiMPEoj+Gtc9K54oNYF44drfTkCYxQQFZUN7
cCJ+FDO3vfhtyGHtrUOZNOuQRgg7Wdmxdm8tLuMbFNTlLWlNo1fcq7TOLlHxXI2e
PAED9Cq8b4cudFetKQIDAQAB
Values explained:
v=DKIM1 = Tells that DKIM version used is version 1
k= key type = Optional but tells which type is used, here it’s RSA
t= flag = here Y equals testing is ON, so DKIM errors will not be rejected, must be removed after testing.
p= Public-key data (base64; REQUIRED) =The key from the rsa-public file you edited earlier in this article.
read more about the DNS parameters here: http://dkim.org/specs/rfc4871-dkimbase.html
After you have set this up, allow for DNS updates to propagate around the world, and test your setup but sending an email to:
This is a free service, which will test your DKIM setup and signatures, and email you a report back.
if there is an error or dns has not updates yet, youwill get:
==========================================================
Summary of Results
==========================================================
SPF check: pass
DKIM check: permerror
SpamAssassin check: ham
But eventually, if you done things right, you get:
==========================================================
Summary of Results
==========================================================
SPF check: pass
DKIM check: pass
SpamAssassin check: ham
After this, you must remove the “t=y;” from the DNS record, to make DKIM “armed”
Hope this helps and don’t hesitate to write me a message, I will gladly help out where I can
Sources: