UPDATE: Enterprise Data Protection is available again from Windows 10 Version 1511 rs1 builds if you want to test Enterprise Data Protection!
UPDATE: Stay on Windows 10 Version 1511 th2 build 10576 if you want to test Enterprise Data Protection!
In this blog I’ll cover a brand new Windows 10 feature, Enterprise Data Protection (EDP). The Microsoft Intune product team recently announced EDP policies as part of the Intune October service update. With this update you’re able to create and deploy configuration policies for Windows 10 enterprise data protection (EDP) settings, such as the list of apps that should be protected by EDP, enterprise network locations, protection level, and encryption using the new Windows 10 Enterprise data protection template.
In a series blog posts I will provide some guidance how EDP works and how to configure protected apps, Configuration Manager and Microsoft Intune.
- Part 1 – Introduction: Enterprise Data Protection – Under the hood
- Part 2 – Retrieve Desktop & Universal Application Information with PowerShell
- Part 3 – Create & Deploy Enterprise Data Protection with System Center Configuration Manager Current Branch (1511)
- Part 4 – Create & Deploy Enterprise Data Protection with Microsoft Intune
- Part 5 – Enterprise Data Protection & Azure RMS better together
In this blog I’ll show you how to configure and apply EDP to your Windows 10 devices. Including some experiences from the field.
Windows 10 by far most secure Enterprise Client Operating System
Enterprise Data Protection is alongside with Microsoft Passport (Hello), Credential Guard and Device Guard one of a kind enterprise grade security features which makes Windows 10 by far the most secure enterprise client operating system available.
Enterprise scenarios
Enterprise Data Protection addresses currently the following enterprise scenarios:
- You can encrypt enterprise data on employee-owned and corporate-owned devices.
- You can remotely wipe enterprise data off managed computers, including employee-owned computers, without affecting the personal data.
- You can select specific apps that can access enterprise data, called “privileged apps” that are clearly recognizable to employees. You can also block non-privileged apps from accessing enterprise data.
- Your employees won’t have their work interrupted while switching between personal and enterprise apps while the enterprise policies are in place. Switching environments or signing in multiple times isn’t required.
Levels of protection
EDP lets you decide to block, allow overrides, or audit your employee’s data sharing actions. Blocking the action stops it immediately, while allowing overrides let the employee know there’s a problem, but lets the employee continue to share the info, and audit just logs the action without stopping it, letting you start to see patterns of inappropriate sharing so you can take educative action. You can set Enterprise Data Protection to 1 of 4 protection levels:
- Block. EDP looks for inappropriate data sharing and stops the employee from completing the action.
- Override. EDP looks for inappropriate data sharing, letting employees know whether they do something inappropriate. However, this protection level lets the employee override the policy and share the data anyway, while logging the action to your audit log.
- Audit. EDP runs silently, logging inappropriate data sharing, without blocking anything.
- Off. EDP isn’t active and doesn’t protect your data.
HKLM\Software\Microsoft\EnterpriseDataProtection\Policies
| Setting | Value | |
| EDPEnforcementLevel | 0 | Off |
| 1 | Override | |
| 2 | Silent | |
| 3 | Block |
Configure Enterprise Data Protection policy
Using EDP you can control the set of apps that are made “privileged apps” or apps that can access and use your enterprise data. After you add an app to your privileged app list, it’s trusted to use enterprise data. All apps not on this list are treated as personal and are potentially blocked from accessing your corporate data, depending on your EDP protection-level.
1. Add new Windows policy and select Enterprise Data Protection (Windows 10 Desktop and Mobile and later). Provide a name and a description followed by configuring protecting apps. You can configure 2 application types, Universal and Desktop apps. In this example I configure a rule for desktop apps and uses the default wildcard.
NOTE! This is not recommended as all applications (executable) are indicated as privileged (insecure) and slows down your system performance!
2. Next step we’ll configure the protection level. In this example we select the Override mode as protection level.
3. Next step we’ll configure the network locations which the privileged apps has access to. Applications which aren’t configured are therefore not able to access corporate resources on these network locations. There are 6 network locations available which can be defined.
- Enterprise Cloud Domain
- Enterprise Network Domain
- Enterprise Proxy Server
- Enterprise Internal Proxy Server
- Enterprise IPv4 Range
- Enterprise IPv6 Range
4. Lastly there are 3 remaining settings available which can be configured. These settings allows you for example to use Azure RMS alongside with Enterprise Data Protection.
5. After we successfully created an Enterprise Data Protection policy we deploy this policies to users with a Windows (Mobile) 10 device.
The User Experience
First thing users will notice – once the Enterprise Data Protection policy became active – is that privileged applications will be identified as managed in the start menu.
Downloading content from a location like SharePoint or a network file share, or an enterprise web location, such as Office365.com automatically determines that the content is enterprise data and is encrypted as such, while it’s stored locally. The same applies to copying enterprise data to something like a USB drive. Because the content is already marked as enterprise data locally, the encryption is persisted on the new device. Privileged applications are notified with an EDP window which indicates the application is protected by your organization.
Once we want to save our document locally – and thus not on a corporate network location defined earlier – the document will automatically encrypted. In this scenario once the document leaves “unintentional” the organization – aka data leakage – the document is by default encrypted and therefore useless.
If we open Windows Explorer you’ll notice the document is encrypted and can be identified by an lock icon. Optionally users are able to manually undo encryption of secured documents, if allowed by your organization.
When copy/paste data from documents which are located on the defined corporate network location(s) users will be prompted that copied data is losing encryption. This applies to an scenario where override protection is configured. If block protection level is enabled users won’t be able to perform the copy/paste action.
Resume
EDP helps protect your enterprise data from leaking to other devices while transferring or moving between them. For example, if an employee puts corporate data on a USB key that also includes personal data, the corporate data remains encrypted even though the personal information remains open. Additionally, the encryption continues when the employee copies the encrypted content back to another corporate-managed device
Enterprise Data Protection under the hood
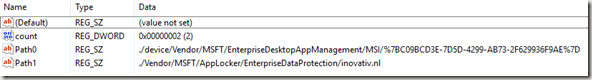
For those who want to have some more insights about how Enterprise Data Protection works on your Windows 10 device hereby some details (eventvwr & registry keys).
HKLM\Software\Microsoft\PolicyManager\current\device\DataProtection
HKLM\Software\Microsoft\EnterpriseResourceManager\Tracked\{GUID}\Device\Default
Windows Event viewer:
- Microsoft Windows EDP Audit Regular Channel
- Microsoft Windows EDP Audit TCB Channel