Tutorial on how to enable Kerberos Authentication in Exchange 2016 base on Configure Kerberos authentication with Exchange 2019.
Enable Kerberos Authentication In Exchange 2016
Kerberos authentication for Exchange’s is not configured by default. The reason is that the shared namespace URL, for example, mail.aventis.dev is not “attached” to a valid computer account.
For Kerberos authentication implementation, we must use an Alternate Service Account (ASA) for the shared namespace URL we are publishing for all Exchange services.
- mail.aventis.dev for MAPI Over Http & Outlook Anywhere (OA).
- mail.aventis.dev for Autodiscover services.
New Computer Object With AES 256 Encryption
- Create an AD Computer Object called EXCHASA
$Password = ConvertTo-SecureString -String "P@ssw0rd!@#$" -Force -AsPlainText
New-ADComputer -Name EXCHASA -AccountPassword $Password -Description ‘ASA for Exchange — DO NOT DELETE’ -Enabled:$True -SamAccountName EXCHASA -Path “CN=Computers,DC=lab,DC=local”
- Enable AES 256 encryption to support Kerberos
Set-ADComputer EXCHASA -add @{“msDS-SupportedEncryptionTypes”=”28"}
- Replicate the changes to all AD Domain Controller
repadmin /syncall /ADPe
Password For Computer Object
- Microsoft Exchange Service Host Service that runs on every mailbox server allows Exchange to work with Kerberos authentication since Exchange 2010 SP1. The only supported way to configure ASA credentials for Kerberos authentication with Exchange servers is running the RollAlternateServiceAcountPassword.ps1 script on every mailbox server.
Run the following on 1st Mailbox Server (lab-ex16.lab.local)
Set-Location $exscripts
.\RollAlternateServiceAccountPassword.ps1 -ToSpecificServer lab-ex16.lab.local -GenerateNewPasswordFor LAB\EXCHASA$
Run the following on 2nd Mailbox Server (lab-ex10.lab.local) and copy the password from 1st Mailbox Server (lab-ex16.lab.local)
Set-Location $exscripts
.\RollAlternateServiceAccountPassword.ps1 -ToSpecificServer lab-ex10.lab.local -CopyFrom lab-ex16.lab.local
Associate SPN With The Computer Object
- Associate SPN with the ASA Computer Account
Setspn -S http/mail.aventis.dev LAB\EXCHASA$
Setspn -S http/autodiscover.aventis.dev LAB\EXCHASA$
#Verify SPN is configured
setspn -L lab\EXCHASA$
Registered ServicePrincipalNames for CN=EXCHASA,CN=Computers,DC=lab,DC=local:
http/autodiscover.aventis.dev
http/mail.aventis.dev
- Verify InternalClientAuthenticationMethod = Negotiate is configured for Outlook Anywhere and IISAuthenticationMethods={Ntlm, OAuth, Negotiate} is configured for MAPI
Get-OutlookAnywhere -Server LAB-EX16 | fl InternalClientAuthenticationMethod
InternalClientAuthenticationMethod : Negotiate
Get-MapiVirtualDirectory -Server LAB-EX16 | fl IISAuthenticationMethods
IISAuthenticationMethods : {Ntlm, OAuth, Negotiate}
- Restart Microsoft Exchange Service Host and MSExchangeAutodiscoverAppPool application pool to speed up the time Outlook will be updated
Restart-Service MSExchangeServiceHost
Restart-WebAppPool -Name MSExchangeAutodiscoverAppPool
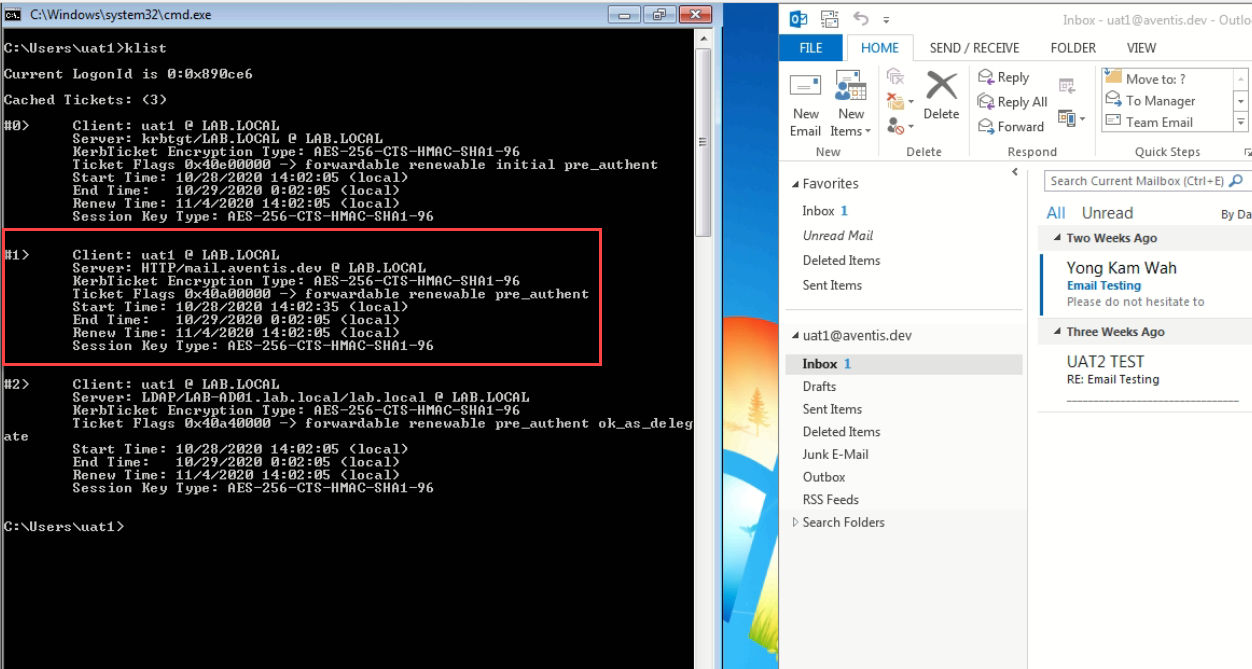
Verify Outlook Is Using Kerberos Authentication
Outlook is connecting to Exchange Server using Kerberos Authentication now