Today I want to have a look at using Azure Conditional Access to restrict external access to Exchange Online OWA. In Azure CA the condition “Client apps” is in preview, with which we can block Exchange Online access using a browser. Combined with the condition “Locations” we are able to only block external access and allow access to Exchange Online using a browser when the user is located on the internal network.
Setting up the Azure Conditional Access policy
Logon to the Azure Portal and browse to Azure Active Directory or Intune. Open the tab Conditional Access and click on +New Policy. The new policy is opened, give your policy a name and click on Users and Groups. Here you need to choose to which users and/ or groups this policy will be applied. It is recommended for testing to pick a group with a small number of users first to test your implementation. If needed you can also select a user or group which will be excluded from the policy.
Next open Cloud apps, mark Select apps, browse for Office 365 Exchange Online and select the Exchange Online app.
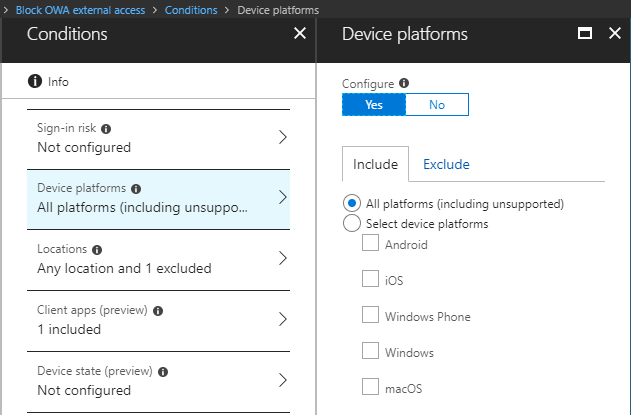
Switch to Conditions and open the Device platforms tab. Here you are able to select on which platforms you want to block access to OWA, in my case I will select all platforms (including unsupported).
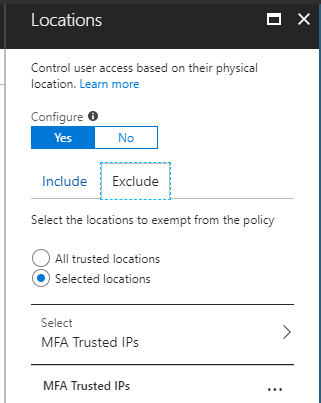
To block external access to OWA, but allow internal access we need to make use of the condition Locations, so open that tab. On the locations tab I select Any location under Include.
Under Exclude I will select MFA Trusted IPs. I have added all my (external) IP addresses from our offices to MFA Trusted IPs, so this will allow OWA access from our internal office networks.
These MFA trusted IPs are managed from Azure AD, Conditional Access, Named Locations.
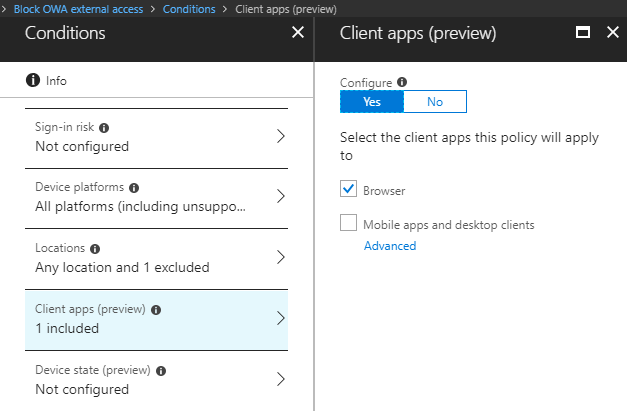
Next switch over to Client apps and only select Browser.
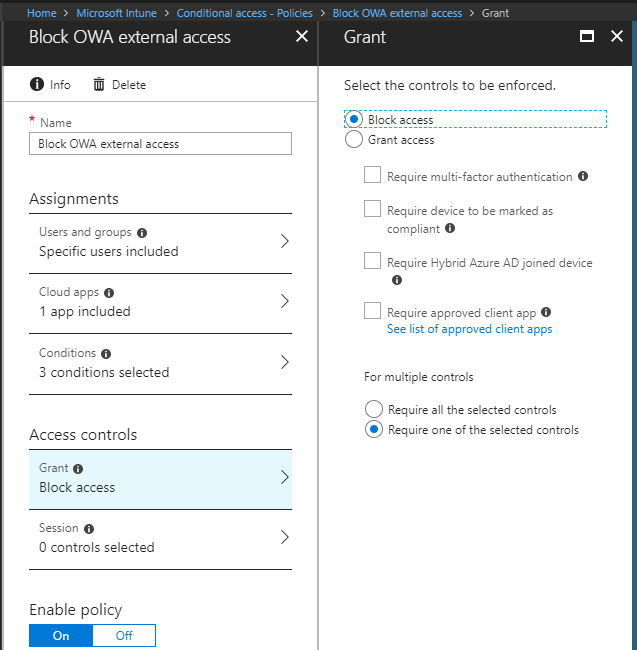
Move on to Access controls. On the Grant tab select Block access, click Select, switch On the policy and click create.
User experience
From an external location, open up a browser and visit https://portal.office.com/myapps
The Office 365 My apps portal is opened. When you click on any of the apps but Outlook, the app is opened. When you click on Outlook you receive a message like below and Outlook (OWA) is blocked.
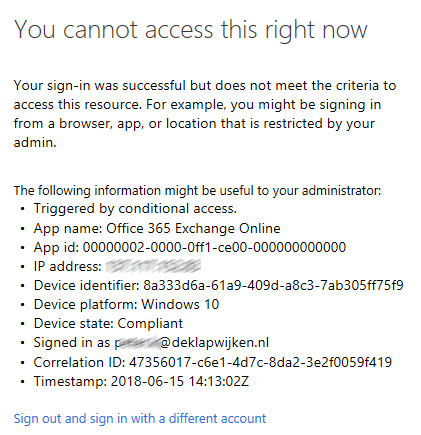
With the option Client apps in Azure Active Directory Conditional Access it is now possible to block OWA access based on IP-addresses without using AD FS.