Problem
Active Directory is built on LDAP, I’ve known this for a long time, but other than it’s a directory protocol that’s about all I did know. Like any directory, if you want information when you query the directory it returns a result. The problem is that information is sent in ‘cleartext’, which is not ideal. To address that you can secure and encrypt that traffic with SSL.
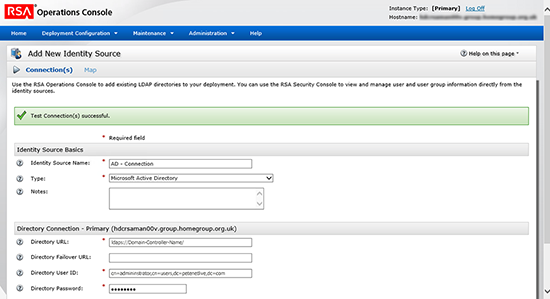
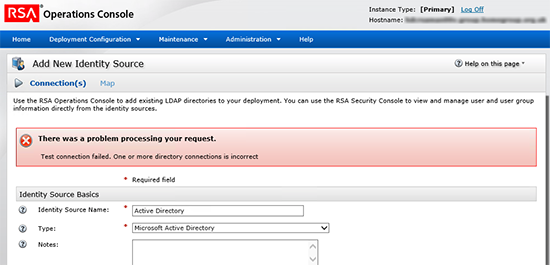
The reason I’m concerned with LDAPS this week, well I was deploying, an RSA Authentication Manager Appliance and when I tried to add Active Directory as an Identity source, this happened;
RSA Operations Console
Add New Identity Source There was a problem processing your request. Test connection failed. One or more directory connections is incorrect.
Solution
To query a domain controller over LDAPS you need a certificate to secure that communication, techies tend to back away when PKI is mentioned, I’m not sure why, but most people fear what they don’t understand, and encryption is pretty complicated,but just think;
- PKI issues certificates to things.
- The certificates make stuff work.
- They expire and need to be renewed.
With that in mind, there are two ways for us to solve this problem. Option 1: Install an enterprise root CA on one of your domain controllers, (that fixes all these problems in one hit). If you only have one server that’s probably our best option, but in any production network thats not a very elegant solution. So Option 2: Is setup a domain PKI solution and use that.
If you already have a PKI/CA infrastructure great, if not, then simply pick a server and launch Server Manager > Manage > Add Roles and Features > Add in the Active Directory Certificate Services role > Follow the on screen prompts.
Actually setting up PKI is outside the scope of this article, I’m running with the assumption that you have a Root/Enterprise CA setup and ready to go.
1. On your CA Server launch the Certification Authority Management Console > Certificate Templates > Right Click > Manage.
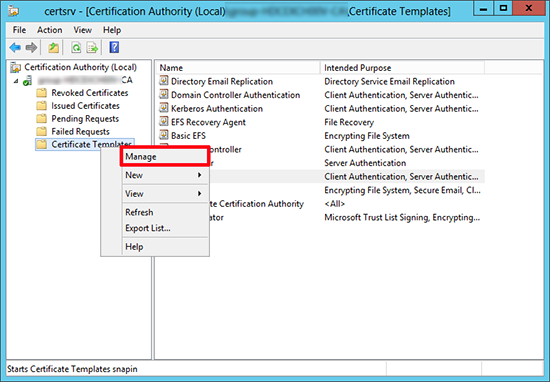
2. Locate the Kerberos Authentication certificate > Make a Duplicate.
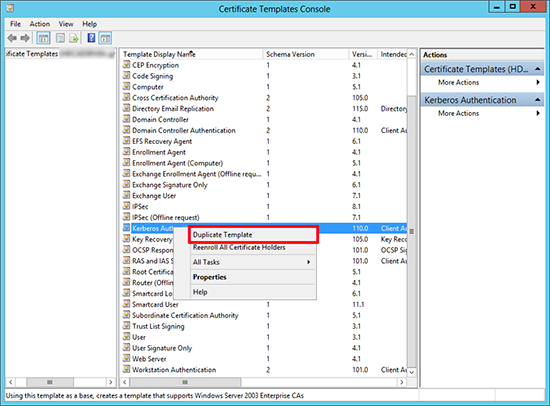
3. General Tab > Call it ‘LDAPoverSSL’ > Set its validity period > Decide if you want to publish the cert in AD.
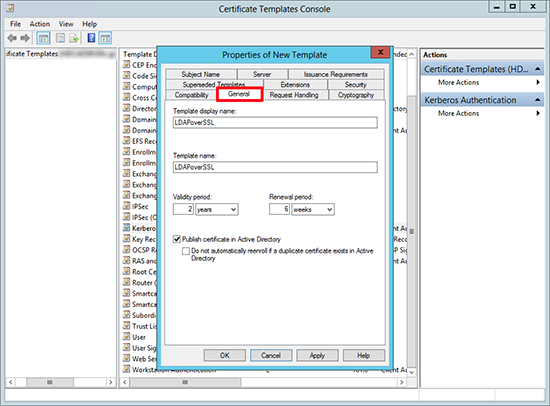
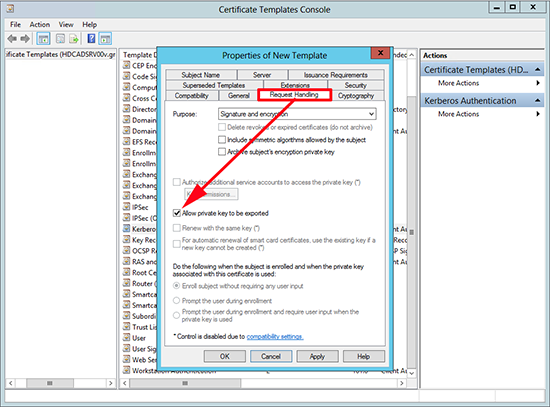
4. Request Handling Tab > Select ‘Allow private key to be exported’ > Apply > OK.
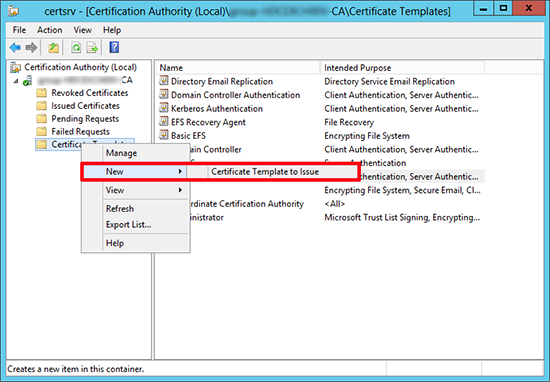
5. Right click Certificate Templates again > Certificate Template to issue.
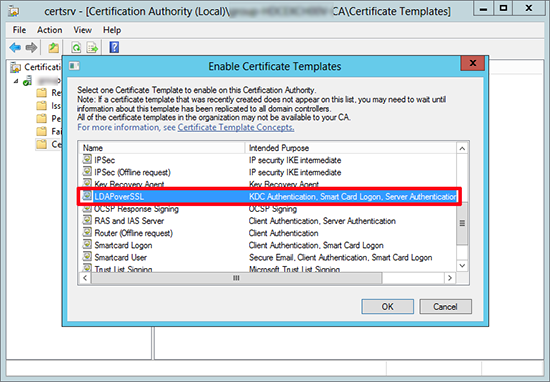
6. Locate and select the ‘LDAPoverSSL’ certificate > OK.
7. Now logon to a DOMAIN CONTROLLER > Windows Key+R > mmc {Enter} > File > Add/Remove Snap-in > Add in the Certificates Snap-In > Computer account > Finish > OK > Expand Certificates > Personal > Certificates > Right Click > All Tasks > Request New Certificate > Next > Next.
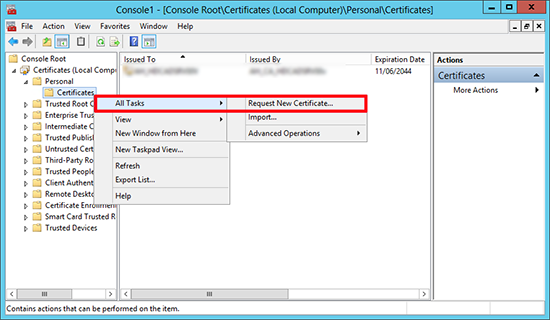
8. Select the LDAPoverSSL Certificate > Enroll > Close the Certificate Snap-in.
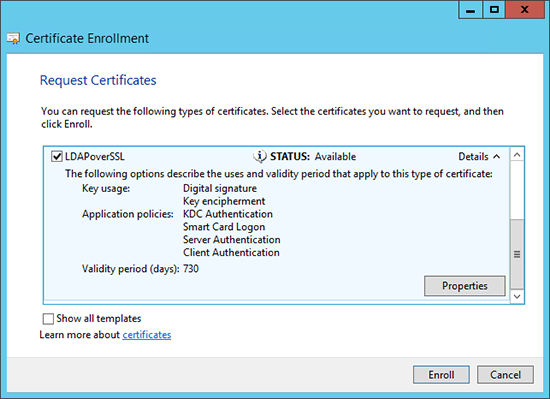
9. In my case I need my device to ‘Trust’ the CA, So on the CERTIFICATE SERVER > open a command window and run the following command;certutil -ca.cert ca_name.cer
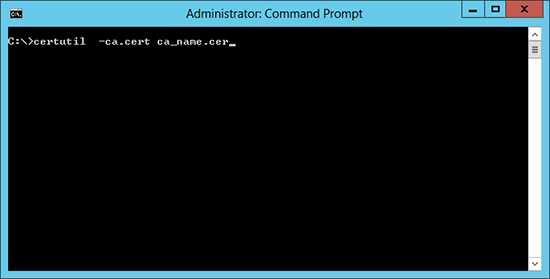
10. It will display the certificate PEM on the screen and should complete successfully.
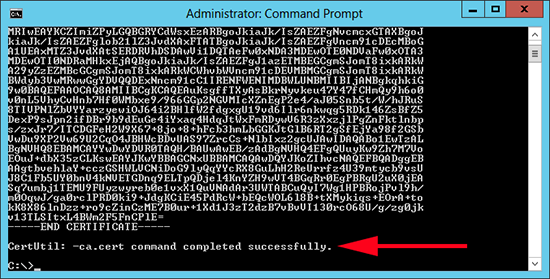
11. You will notice my command was run while I was on the root of the C: Drive, yours will probably be C:Users{your-username} go there and retrieve a copy of the ‘Root Certificate’.
Testing LDAP and LDAPS
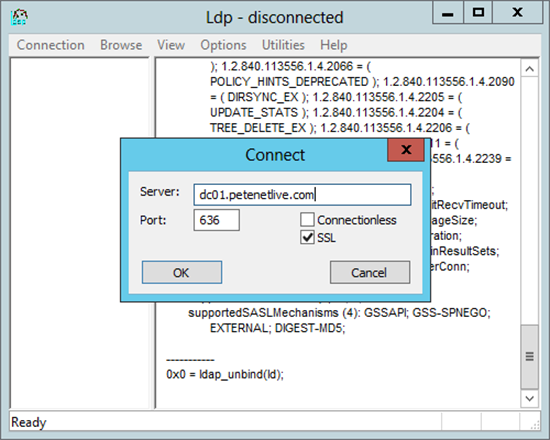
12. On another server > Open a command windows and run ldp > Connection > Connect > Type in the FQDN of the DC > Set the port to 636 > Select SSL > OK > It should return some results
Note: If you get an error you may need to reboot the domain controller.
That’s your DC configured (You can repeat the process for further DC’s), but remember Imtrying to connect my RSA Appliance.
Adding Active Directory to RSA Authentication Manager
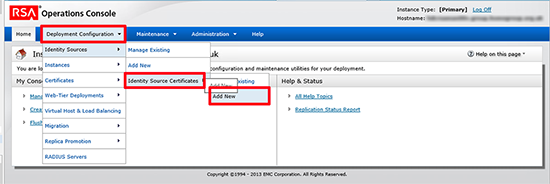
13. Log onto the Operations Console (https://{fqdn}/oc) Deployment Configuration > Identity Source Certificates > Add New > Add in the Root-Cert you exported above.
14. This time when I add my Active Directory as an Identity Source, it completes without error.